Your website is clearly protected by Cloudflare, so why is it still hacked?

Your website is clearly equipped with Cloudflare protection, so why is it still hacked? ?The culprit may be this DNS configuration vulnerability! The Cloudmare artifact I want to introduce today is like a "cloud shield detector", which can uncover the wrongly configured source station IP in 3 steps! (Practical tutorials are attached at the end of the article)
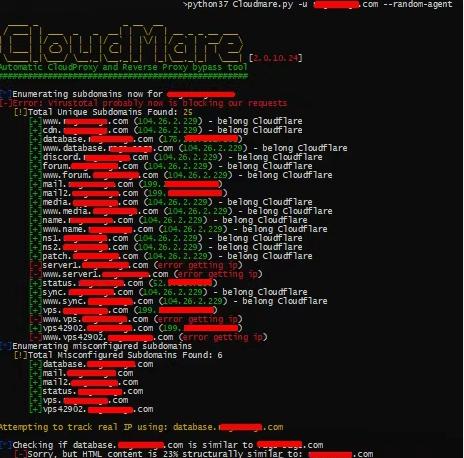
(The schematic diagram has been desensitized, please eat it with confidence~)
This open source tool can detect with one click: ✅ Cloudflare/Sucuri/Incapsula Protection Site
✅ DNS resolution configuration error
✅ Real IP exposure risk of source server
? Get started in five minutes quickly
1️⃣ Clone Arsenal
git clone https://github.com/MrH0wl/Cloudmare.git
cd Cloudmare?Xiaobai can also understand: it is like downloading a toolkit to your computer
2️⃣ Turn on the scan mode
python Cloudmare.py -u Your website.com --bruter -sC?High-level skills: Adding the -sSh parameter can also detect SSL certificate vulnerabilities!
3️⃣ View the results
Report interpretation guide:
?Red alarm → Must be fixed immediately
⚠️Yellow warning → Optimized configuration
? Android User Exclusive Guide
? class="page_speed_1018338877">Use Termux mobile phones to become a hacker (tutorial simplified version):
Installing the "Hacking Three-Piece Set":
pkg install git python dnsutils
One-click run:
git clone https://github.com/MrH0wl/Cloudmare.git cd Cloudmare && python Cloudmare.py -hh
?Tip: For the first time, you must be patient and then automatically install plug-ins~
✔️ Run Cloudmare regularly to detect its own website
✔️ Turn off non-essential DNS resolution records
✔️ Whitelist of source site IP binding access
✔️ Enable Cloudflare's "strict mode"